Network Segmentation Techniques
As someone who’s spent time diving deep into network design and security, I often get asked: What’s the best way to segment my network? The answer isn’t always straightforward because it depends on your hardware, goals, and security requirements.
Today, I want to unpack three key segmentation techniques: VLANs, VRFs, and Virtual Domains (VDOMs) from the perspective of different vendors and device types. Plus, I’ll share which approach I think is superior for specific use cases.
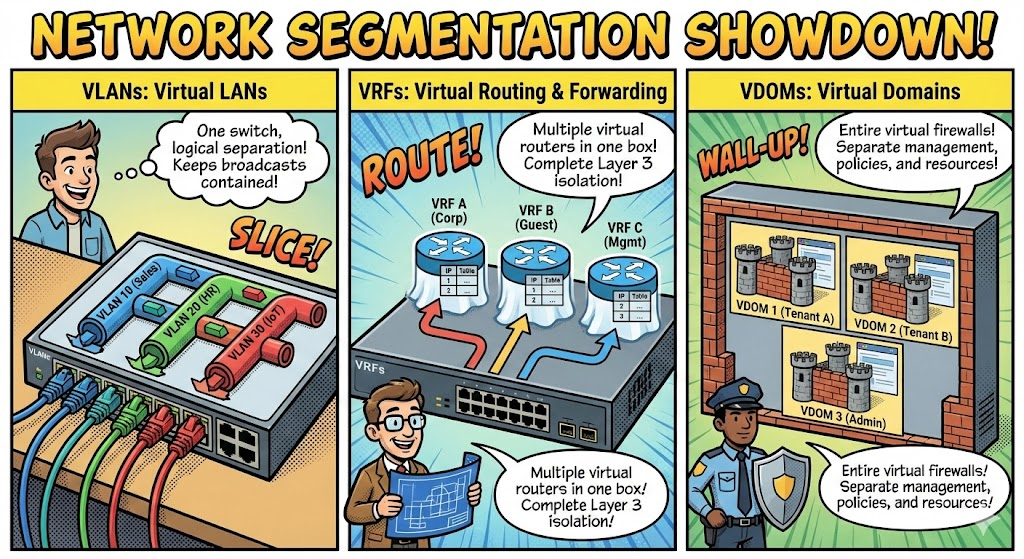
VLANs: The Classic Workhorse for Switches and Basic Segmentation
Where you find it: VLANs are ubiquitous in switches (Cisco Catalyst, Juniper EX, Arista EOS, HPE Aruba) and are often the first step in network segmentation.
What they do: VLANs segment your Layer 2 network by separating broadcast domains using tagging (802.1Q).
Management interface segmentation: VLANs are typically the recommended method here, especially on switches. You isolate management traffic on dedicated management VLANs, often combined with ACLs to restrict access.
Vendor recommendations:
- Cisco Switches: Use VLANs combined with private VLANs and 802.1X for port-based access control.
- Juniper EX: Emphasize VLANs with strong security policies at Layer 2.
- Arista EOS: Supports VLANs extensively with additional overlay capabilities.
- HPE & Extreme: Recommend VLANs for both data and management plane segmentation.
My take: VLANs are simple, widely supported, and effective for basic segmentation, but they don’t inherently provide Layer 3 routing separation. For that, you need VRF or firewall segmentation.
VRF: The Layer 3 Powerhouse on Routers and Firewalls
Where you find it: VRF is supported on routers (Cisco ISR/ASR, Juniper MX, Arista routers) and firewalls (Fortinet FortiGate, Cisco Firepower, Juniper SRX).
What it does: VRFs create multiple isolated routing tables on the same device. This means overlapping IP address spaces can coexist without conflict, and routing isolation is enforced at Layer 3.
Management interface segmentation: Vendors often recommend dedicating management interfaces to specific VRFs to strictly isolate management traffic from user or tenant traffic.
Vendor recommendations:
- Cisco Routers/Firewalls: VRFs are the go-to for multi-tenant and secure routing isolation; management VRF for admin traffic is strongly recommended.
- Juniper MX/SRX: Use routing instances (VRFs) with granular policy controls and dedicated management VRFs.
- Fortinet Firewalls: VRFs are used for separating security zones and management planes.
- Arista EOS: VRFs are standard for data center routing and management segregation.
My take: VRF offers superior isolation compared to VLANs because it operates at Layer 3 and ensures no routing leakage between segments. For any environment requiring strong tenant or admin separation, VRF is essential.
Virtual Domains (VDOMs) and Virtual Systems: Multi-Tenant Firewalls on Steroids
Where you find it: VDOMs are primarily Fortinet FortiGate firewall technology, while similar concepts exist as virtual systems (vsys) on Palo Alto Networks firewalls, virtual contexts on Cisco ASA, Firepower, and Juniper SRX.
What it does: VDOMs partition a single firewall device into multiple independent virtual firewalls, each with its own policies, routing, and management. This provides administrative and security separation within one physical box.
Management interface segmentation: Each VDOM or virtual system has dedicated management interfaces and policies. Vendors recommend isolating management traffic per virtual domain for security and compliance.
Vendor recommendations:
- Fortinet FortiGate: VDOMs are highly recommended for MSPs and enterprises needing multi-tenant firewall separation.
- Palo Alto Networks: Vsys offers similar multi-tenant capabilities.
- Cisco Firepower & Juniper SRX: Use virtual contexts/systems for multi-tenant isolation.
My take: VDOMs and virtual systems are superior when your goal is secure multi-tenant firewalling without deploying multiple devices. They add complexity but offer unmatched administrative separation and policy granularity.
Which Segmentation Technique is Superior?
| Segmentation Type | Device Type | Best For | Management Segmentation Approach | Strengths | Limitations |
|---|---|---|---|---|---|
| VLANs | Switches | Basic Layer 2 segmentation | Separate management VLANs | Simple, widespread support | Limited Layer 3 isolation |
| VRF | Routers, Firewalls | Layer 3 tenant/routing isolation | Dedicated management VRFs | Strong routing isolation | Complex config, needs care |
| VDOMs / Virtual Systems | Firewalls (Fortinet, Palo Alto, Cisco, Juniper) | Multi-tenant firewall segmentation | Dedicated management per VDOM/vsys | Full admin & security isolation | Increased management overhead |
Final Thoughts: Segmentation in Multi-Environment Networks
In real-world networks, especially those with distinct production, staging, and testing environments, segmentation needs go beyond basic VLANs. Simply tagging traffic into VLANs often falls short because it only separates at Layer 2 and can’t fully prevent traffic leakage or enforce strict routing policies between sensitive environments.
This is where Cisco ASA’s context mode (virtual firewall instances) and VDOMs on Fortinet FortiGate truly shine. Both technologies allow you to create fully isolated firewall instances on a single physical device, each with independent policies, routing, and management access. This level of separation means you can confidently isolate your production environment from staging and testing, preventing accidental cross-contamination and improving security posture dramatically.
Why is this superior to VLANs?
- VLANs can be bypassed or misconfigured, potentially allowing traffic to leak between environments.
- VRFs and VDOMs enforce strict Layer 3 and policy separation.
- Each virtual firewall instance can have unique security policies tailored for the environment’s risk level.
- Management and logging are isolated per environment, aiding compliance and troubleshooting.
Vendors and Virtual Domain Support
While enterprise vendors like Cisco, Fortinet, Palo Alto Networks, and Juniper fully support VRFs and virtual domains/contexts, some popular vendors do not offer this level of multi-tenancy:
- Ubiquiti UniFi: Primarily relies on VLAN-based segmentation; no support for VRFs or VDOMs.
- TP-Link, Netgear, and other SMB vendors: Typically focus on VLANs and basic ACLs, lacking advanced virtual domain features.
- MikroTik: Supports VRFs, but not virtual firewall domains akin to Fortinet VDOMs.
If your environment requires strict, secure separation of multiple environments on the same infrastructure, choosing hardware that supports VRF or virtual domains is critical.
In Summary
For segmented environments spanning production, staging, and testing:
- Use VLANs for simple Layer 2 segmentation but do not rely on them alone for security.
- Leverage VRFs on routers and firewalls to isolate routing and management planes.
- Deploy VDOMs or firewall virtual systems on devices like Fortinet FortiGate or Cisco ASA for true multi-tenant firewall separation.
This layered approach ensures each environment remains secure and manageable while reducing complexity and hardware footprint.
Need help architecting your network design and segmentation strategy? Feel free to reach out!